When the Stuxnet computer worm attacked programmable logic controllers (PLCs) at Iranian nuclear facilities running an integrated solution, centrifuges were commanded to literally rip themselves apart. This clear demonstration of the link between cybersecurity and safe industrial operations was a worldwide wake-up call for plant managers, IT and automation experts, safety engineers and many others.
Cybersecurity and plant safety
Path to a safe, secure facility
When the Stuxnet computer worm attacked programmable logic controllers (PLCs) at Iranian nuclear facilities running an integrated solution, centrifuges were commanded to literally rip themselves apart. This clear demonstration of the link between cybersecurity and safe industrial operations was a worldwide wake-up call for plant managers, IT and automation experts, safety engineers and many others.
Of course, smaller-scale attacks are much more likely, and they are happening. At one plant, where system maintenance was done remotely, an attack from abroad revealed the weakness of using simple username/password authentication for remote access. The attack was discovered only after the data transmission volume exceeded the company’s data plan.
Cyber-related safety vulnerabilities aren’t necessarily the result of criminal activity. Du-ring the commissioning of one plant, for example, the failure of engineering software during the recompiling of the memory mapped input (MMI) following a plant shutdown led to an incorrect modification being loaded into an integrated safety controller and subsequently activated.
All three examples demonstrate the need for specific IT security improvements and raise bigger questions about the relationship between cybersecurity and plant safety:
- Can the “insecurity” of integrated control systems influence the functional safety of a plant?
- What needs to be protected?
- Can the principles developed for functional safety be applied to security?
This article considers these questions, then describes a few operational examples and specific recommendations for improving security and safety at industrial facilities.
International standards
IEC 61508 is the international standard of rules for functional safety of electrical, electronic and programmable electronic safety-related systems. According to IEC 61508, functional safety is “part of the overall safety that depends on functional and physical units operating correctly in response to their inputs”.
By this definition, the answer to the first question – can the “insecurity” of integrated control systems influence the functional safety of a plant? – has to be “yes”. In the examples cited above, vulnerabilities to people and facilities were introduced. Clearly, functional safety was compromised, and while security compromises may not have led to deaths or injuries, there is no evidence to suggest that could not occur in the future.
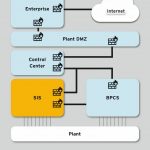
Even if malicious threats are ruled out, the fact remains that IT-security-based vulnerabilities can be found in all kinds of automation systems. These include the safety-related system itself and the distributed control system (DCS), of which the safety system may be a part. This is one reason why so many safety experts call not only for the physical separation of safety instrumented system (SIS) and DCS components, but also for different engineers and/or vendors to be responsible for each.
To answer the other questions, we need to highlight two other standards. One is the international IEC 61511 standard for the SIS. Whether independent or integrated into an overall basic process control system (BPCS), the SIS is a fundamental component of every industrial process facility.
In this model the industrial process is surrounded by different risk reduction layers which collectively lower the risk to an acceptable level. The risk reduction claim for the different layers is set by the safety integrity level (SIL).
The first line of protection for any plant is the control and monitoring layer, which includes the BPCS. By successfully carrying out its dedicated function, the BPCS reduces the risk of occurrence of unwanted events. Typically, IEC 61511 stipulates that the risk reduction claim of a BPCS must be greater than 1 and less than 10. A risk reduction capability of 10 equates to SIL 1.
The prevention layer includes the SIS. The hardware and software in this layer perform individual safety instrumented functions (SIFs). The risk reduction factor to be achieved by the prevention layer is determined during the risk and hazard analyses carried out as part of the basic design process of every plant.
In most critical industrial processes, the SIS must be rated SIL 3, indicating a risk reduction factor of 1000, to bring the overall risk down to an acceptable level.
Technical systems are allocated at the mitigation layer, allowing mitigation of damages in case the inner layers of protection fail. In many cases mitigation systems are not encountered as being part of the safety system as they are only activated after an event (that should have been prevented) has happened. However, in instances where the mitigation system is credited as part of defining additional measures, it may be covered by the safety evaluation as well.
Let us now consider the IEC standard for cybersecurity. IEC 62443 (currently in draft form) covers the safe security techniques necessary to stop cybersecurity attacks on facility networks and systems.
Norms and structures require protection
Now back to the second question: what needs to be protected? According to the most recent version of IEC 61511, the answer is that both norms and physical structures are in need of protection. As far as norms are concerned, the standard calls for the following:
- Security risk assessment of the SIS
- Sufficient resilience of the SIS against the identified security risks
- Security of the SIS system performance, diagnostics and fault handling, protection from unwanted programme alterations, data for troubleshooting the SIF and bypass restrictions so that alarms and manual shutdown are not disabled
- Enabling/disabling of read/write access via a sufficiently secure method
As for the structural requirements, IEC 61511 instructs operators to conduct an assessment of their SIS related to the following:
- Independence between protection layers
- Diversity between protection layers
- Physical separation between different protection layers
- Identification of common-cause failures between protection layers
Another IEC 61511 note has particular bearing on the issue of cybersecurity and plant safety: “Wherever practicable, the SIF should be physically separated from the non-SIF.”
Independent layers of protection
Question number 3 asks “can the principles developed for functional safety be applied to security?”.
The IEC 61511 (safety) and IEC 62443 (security) standards concur regarding the demand for independent layers of protection. Together these standards prescribe:
- Independence of control and safety
- Reduction of systematic errors
- Separation of technical and management responsibility
- Reduction of common-cause errors
The standards also emphasise that anything and everything within the system is only as strong as its weakest link. When using embedded safety systems, all hardware and software that could impair the safety function should be treated as being part of that safety function.
IEC 61511 specifies different, independent layers of protection. Unifying two layers of protection will necessitate a new risk-reduction evaluation proving compliance with the overall risk reduction that would be achieved with two different protection layers.
Recommendations
Cybersecurity and plant safety are so intertwined in the connected world of industrial processes that an equal commitment to both is required to achieve the needed protection. Following the recommended international standards for functional safety for PLCs (IEC 61508), safety instrumented systems (IEC 61511) and cybersecurity (IEC 62443) provides a path to a safe, secure facility.
For the most robust security and reduced safety risks, Hima advocates the traditional approach of standalone SIS and BPCS units – ideally from different vendors – versus an integrated BPCS/safety system from the same vendor.
For valid security and safety reasons, Hima also encourages companies to consider an independent safety system built on a proprietary operating system. Of course, such a system can and should be completely compatible with DCS products. Additionally, it should feature easy-to-use engineering tools with fully integrated configuration and programming.
www.cpp-net.com search: cpp0116hima
Peter Sieber
Peter Sieber
Vice President Global Sales & Regional Development, Hima
Share: